We have improved VulnDB API and have a new (and better) Help site. Read on to find out more about these changes.
VulnDB HQ is a tool to manage your vulnerability descriptions so you can reuse them across reports. It also lets you create and share testing methodologies so every project is delivered to the same high quality standard.
We have recently migrated the VulnDB Help site to a new location at:
Apart from the new look & feel (which we hope you like) we’ve made a few significant improvements in the API itself:
Strict SSL requirement
The API was accessible over plain-text HTTP due to a misconfiguration, we have completely disabled this.
Token-based authentication
Say your goodbyes to HTTP Basic authentication and welcome the new token-based authentication overlords.
Visit your Profile page to get your own API token which can be used to authenticate API request by means of a custom HTTP header.
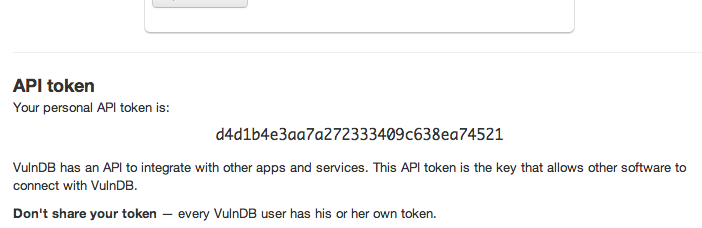
Lost your token or you suspect it was compromised? Want to deny access to your account to all 3rd party applications? Regenerate your token and you are good to go.
Better examples
We’ve improved the examples for each of the API methods with a proof-of-concept `curl` request along with the sample of any data that has to be submitted to the request. We also show response codes and content returned by the server so you know what to expect.
tl; dr;
Find answers to your VulnDB API questions at http://vulndbhq.com/help/
Note that we have not bumped the version number to introduce these changes. This is because the main interfaces, media formats, end points and data types have not changed.